Robocalls and telemarketing calls are currently the number one source of consumer complaints at the FCC. What was once a nuisance has become a plague to U.S consumers receiving an estimated “16.3 billion robo-calls in the first five months of 2018. In May 2018, U.S. people received about 4.1 billion robocalls or 12 calls for every person.”
The FCC has been encouraging service providers to offer call blocking solutions that give customers greater control over the types of calls they receive. Call blocking is one part of the robocall solution. Another part is identifying the bad actors who use robocalls to take advantage of unsuspecting consumers by using numbers assigned to others (spoofing). They use cheap and accessible technologies to spoof their caller identity and scam victims with threats from the IRS and offers of loans or free travel.
Although several providers and third parties offer call blocking and caller identification verification products, there is no ubiquitous solution that spans wireline and wireless communication networks. In order to address these concerns, the service providers are focusing their efforts across three key areas: source authentication as well as network and consumer blocking tools. The goal of these solutions is to protect the consumers from unwanted calls and give them more control over the calls and texts they receive.

STIR/SHAKEN Definitions
STIR (Secure Telephony Identity Revisited) is the proposed standard developed by IETF that defines a signature to verify the calling number, and specifies how it will be transported in SIP “on the wire.”
SHAKEN (Signature-based Handling of Asserted information using toKENs) is the framework document developed by the ATIS/SIP Forum IP-NNI task force to provide an implementation profile for service providers implementing STIR. STIR/SHAKEN will be the basis for verifying calls, classifying calls and facilitating the ability to trust the caller ID information.
Caller Authentication
The idea behind of STIR/SHAKEN is to mitigate unwanted robocalls and bad actors who use caller ID spoofing to increase the chances of speaking to a subscriber.
STIR is used to enhance the SIP protocol to provide a mechanism for service providers to verify that the originator of a SIP call is highly likely to be valid (i.e. not a spoofed/fraudulent calling party). The goal of these enhancements is to make it considerably more difficult for bad actors to spoof the identity of a call for malevolent or other purposes. Examples of such activities are spoofing voice messaging or credit card validation services to get access to the victim’s voice messages or credit, respectively; engaging in confidence schemes by masquerading as legitimate enterprises looking for information or cash (e.g., banks for personal identification or the IRS for swindling); or to get through blocked caller lists (e.g., robocalling).
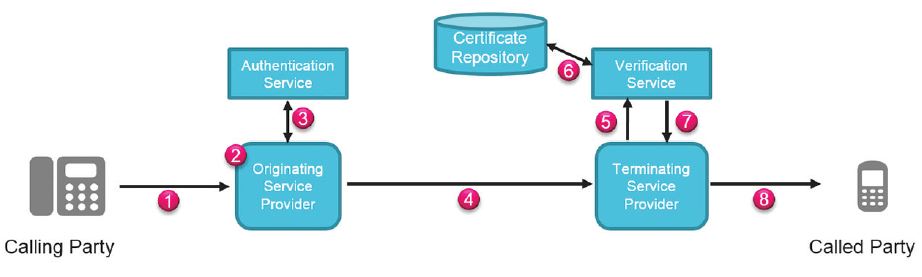
STIR mitigates these problems, but is not designed to provide a 100% solution. Moreover, STIR does not work in all call scenarios. The following table is a summary of the call scenarios and STIR’s contribution to the mitigation of the caller ID spoofing problem.
STIR Calling Scenarios in the U.S.
In short, STIR was initiated in the U.S. to address compromised identities in SIP-signaled networks. And, the specifics of how the authorization mechanism works, for all practical purposes, will be a U.S.-centric solution for the foreseeable future. “This is because the approach requires one to trust the certificate authority issuing the signing credentials. That is an issue of policy, not technology. As such, that will require industry agreement or regulation, which by its nature will be dealt with by the various national telecommunications authorities.”
From a technology perspective, there is no way of using the mechanism in a reliable manner for PSTN-originated calls. A PSTN-originated call would be coming from a legacy class 5 or PBX switch to a media gateway. There is no technical way of proving the origin of the compromised caller ID or billing number (ANI) of a call in the PSTN. That is why this issue continues to exist. There could be administrative ways of improving the origin of the compromised caller ID coming from the PSTN, such as if the access carrier will vouch for the veracity of the caller ID. This would be possible for those carriers who would be willing to verify that calls originating in their network have valid caller IDs. “As such, the (STIR) mechanism does offer the potential to mitigate some PSTN-originated calls that have SIP gateways ‘close’ to the origination or where the trunk sources can be identified. In addition, international gateways could mark calls with numbers being asserted as a calling party number from the North American Numbering Plan (NANP), but originating from outside the NANP, as suspect.”
Ribbon’s Solution for STIR/SHAKEN
SBC and PSX for Caller Authentication and Verification
Ribbon’s solution, which consists of its SBC and PSX, has been validated on its effectiveness of the caller authentication standards developed by the Internet Engineering Task Force (IETF) and the Alliance of Telecommunications Industry Solutions (ATIS).
In this STIR/SHAKEN solution, the SBC will generate and pass an identity header/signature to an authentication server via the Ribbon PSX. The PSX will receive verification of the signature and pass that back to the SBC. The SBC has flexible handling of error conditions, e.g. “reject the call”, “continue with the call”, “continue with the call and remove Identity header” if signature verification fails.
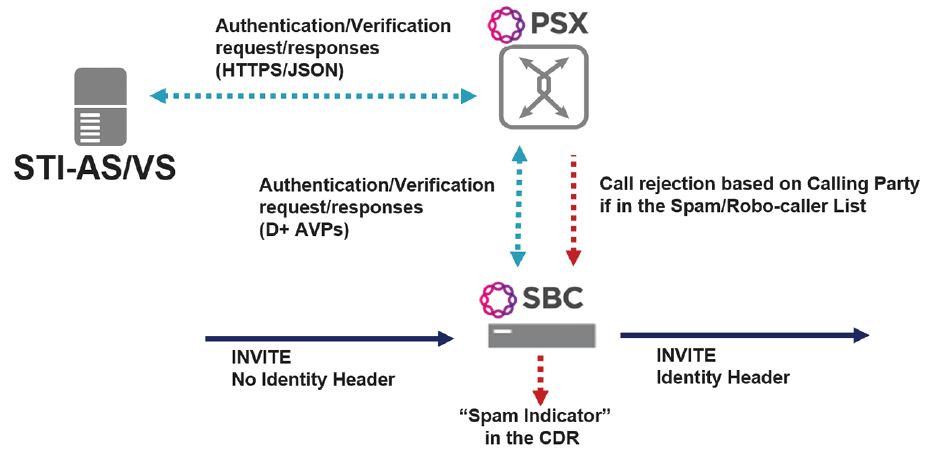
Notable Functions
- STIR/SHAKEN is applicable to the SBC Core product line: SBC 5000 series, SBC 7000, and SBC SWe
- SBCs can be configured to handle call signing process differently based on trusted/untrusted peering partner relationships
- Calls from “trusted” partners: Signature is generated through the PSX and corresponding Identity Header is inserted by the SBC if the initial INVITE does not include Identity header yet.
- Calls from “untrusted” partners: SBCs can be configured to bypass the signing/identity header insertion process and forward the call or obtain a signature if the initial INVITE does not include Identity header yet.
- Verification of signature is performed through the PSX upon receipt of an Identity header for an ingress call from another operator/network.
- SBCs can be configured to either forward or drop the call for failed authentication
- SBCs have flexible and configurable handling of error conditions such as: call rejection, forward the call, forward the call and remove identity header if signature verification fails.
- All error conditions are stored in the SBC call detail records for subsequent analysis
Summary on the STIR/SHAKEN Solution
Although several providers and third parties offer call blocking and caller identification verification products, there is no ubiquitous solution that spans wireline and wireless communication networks. In order to address these concerns, the service providers are focusing their efforts across three key areas: source authentication as well as network and consumer blocking tools. Ribbon is leading the way with advanced solutions to protect consumers from unwanted calls and give them more control over the calls and texts they receive.

