Analytics & Voice Security Products
Powerful Visualization, Analyzing, Troubleshooting, and Threat Prevention
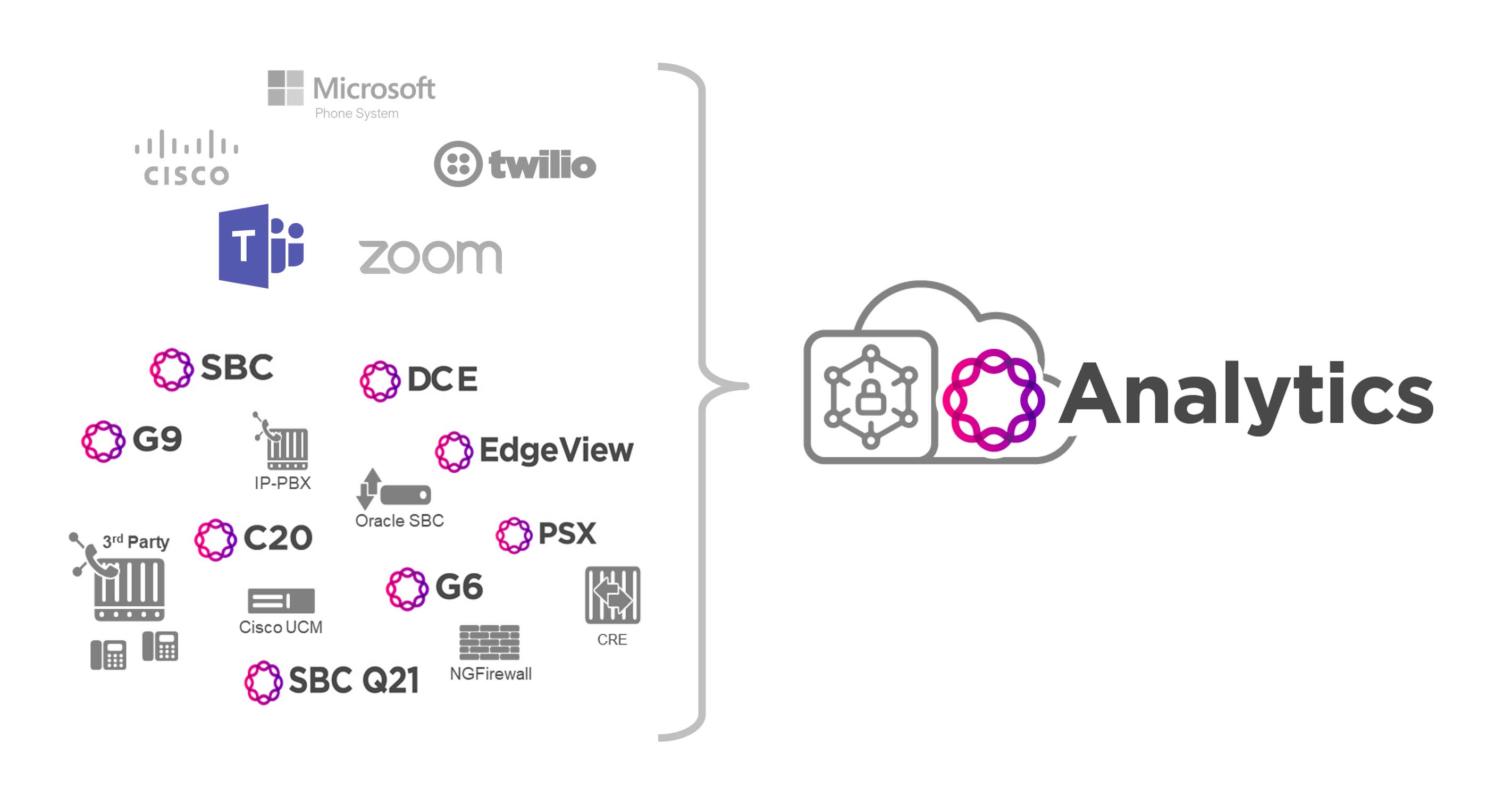
Businesses need powerful, flexible, and easy-to-use analytics tools to visualize and monitor network performance.
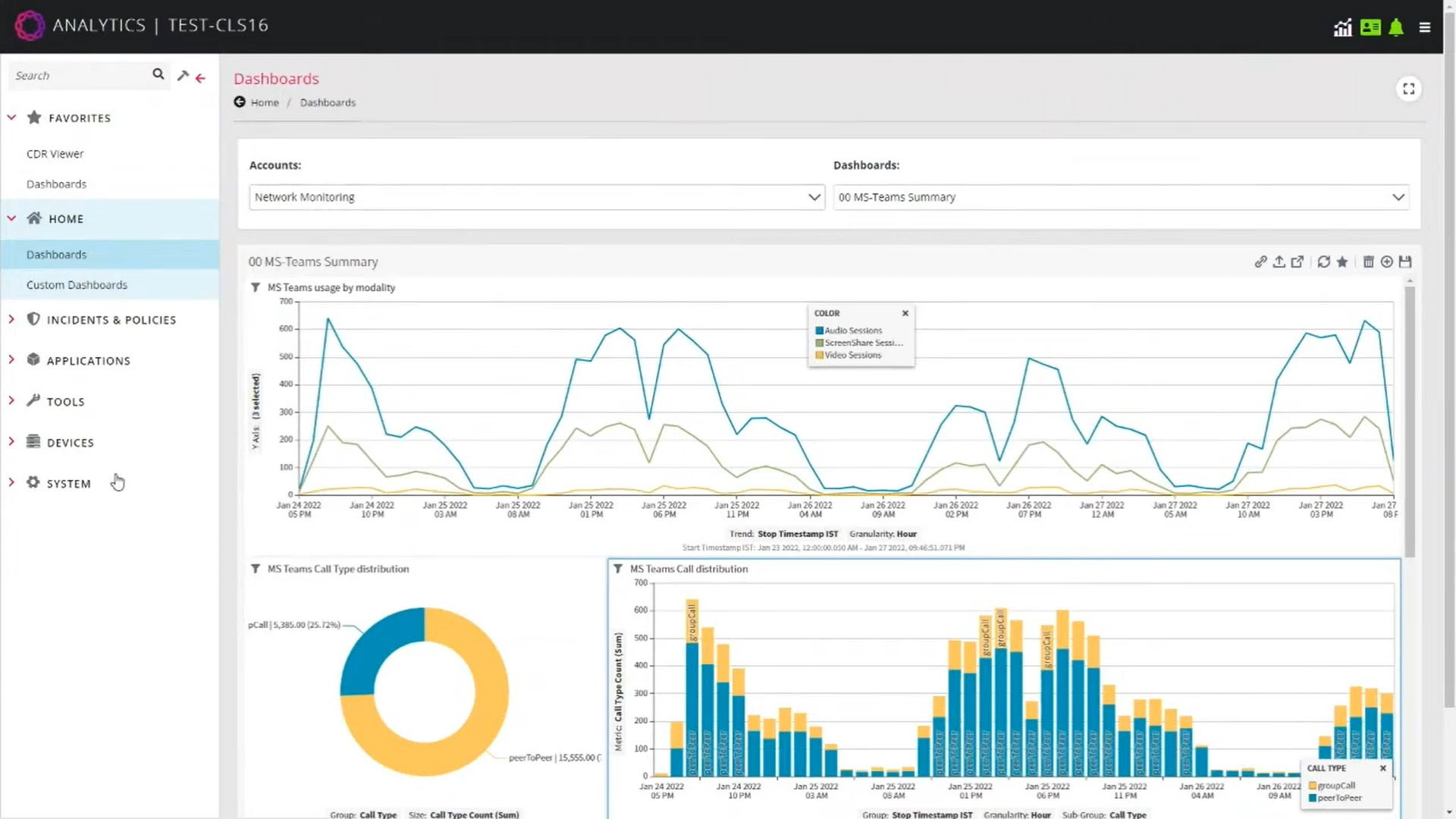
With Ribbon Analytics in your network, you will be able to monitor the network for KPIs and key trends as well as secure, troubleshoot, and alert on QoE issues. This provides many benefits such as end-to-end network visibility, improved operational productivity and efficiency, faster troubleshooting, service issue identification and resolution, and security.
Read a Solution Brief on our Ribbon Analytics: Application Portfolio.
View the PortfolioDownload MPC Solution Brief
Ribbon Analytics Demos
Demos that show you how to be in charge of your voice network and Microsoft Teams Calling!
Operations Analytics
bolt
Operational Efficiency
Increasing Network Visibility
Avoiding Service Disruption
ML-Based Network Planning, Troubleshooting & Management

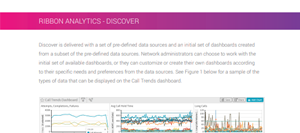
Dashboards
Summarize network or service analysis
KPIs to understand network behavior
Correlation of collected data pointsRules & incident detection
Visibility into network performance and quality issues to pinpoint abnormalitiesAlerts and policies
Based on trigger settings
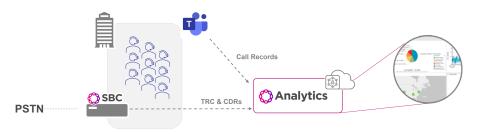
Visibility, Assurance and Analytics for Microsoft Teams
-
Transforming Raw KPIs into Actionable Insights
-
Visualizing RTC Service Quality Characteristics
-
Detecting Potential Issues Before They Impact End-Users
Gain end-to-end visibility and Intelligence into your communications networks, devices, and users
Proactively Manage Your Team's Experience
Security Analytics For Voice Threat Prevention
lock
Security
Evolving Network Attacks & Threats
Reduce Attack Surfaces, Detection & Mitigation
Avoid Lost Customer Trust

Behavioral analytics has made a noticeable impact in the overall security threat detection community. However, the Unified Communications (UC) and Contact Center (CC) community is still largely underserved regarding behavioral analytics and threat detection. With the variety and inherent complexities of SIP and VoIP protocols, UC/CC environments will benefit greatly from the added value of behavioral analytics and threat detection to identify and prevent many types of fraud or theft.
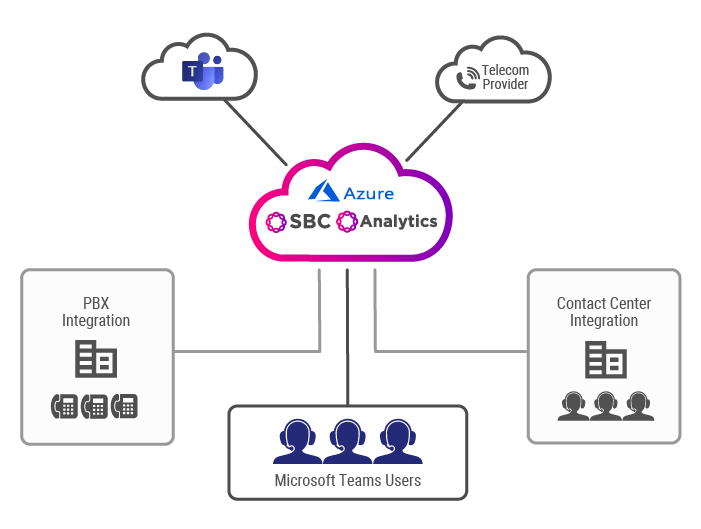
Yet, even with behavioral analytics and anomaly detection, assuring the integrity of UC/CC services usually means an enterprise IT team will need both visibility and control over a variety of disparate products. Unfortunately, these disparate products will rarely, if ever, interact with each other for security purposes. Ribbon solves the security isolation issue by taking a unique integrated approach that collects data from multi-vendor network elements and analyzes this data for anomalies that would indicate voice threats.
Identification of potential attacks on an enterprise's UC/CC network or services and the bad actors initiating these attacks is forwarded to Ribbon's cloud-hosted Reputation Scoring service that determines, in real-time, if a given SIP session is likely malicious and what is the ideal policy to mitigate the specific threat. Policy decisions drive real-time policy enforcement across various security domains, in real-time before a threat disrupts business or causes loss of confidential data or finacial loss. Significant reduction of the overall threat landscape is possible with a voice threat prevention
Security Portfolio Overview Download Voice Threat Prevention Brief
Security, Network Visibility and Big Data Analytics Solutions
Secure your UC Network - Ribbon Security
Enterprise Scale Real-Time Communications Analytics
Benefits
- Stay ahead of outages
- Fix issues faster
- Gain immediate ROI
- Manage growing networks
- Identify Security Threats
- Justify upgrades
- Report on SLAs
Watch the Analytics Webinar
Related Content
Learn more about Ribbon Analytics