STIR/SHAKEN Standards
To overcome the influx of unwanted calls in the service providers network, the industry has created two new standards: STIR (Secure Telephone Identity Revisited) and SHAKEN (Signature-based Handling of Asserted information using toKENs) standards. Together, these two standards, create the framework to ensure every SIP-signaled call has a certificate of authenticity attached to it — a digital signature — that allows service providers verify caller ID to mitigate unwanted robocalls and prevents bad actors from using Caller ID spoofing. With STIR/SHAKEN, service providers can restore their end customer’s trust in validity of caller ID.
Ribbon Support for STIR/SHAKEN
Service providers can choose between two Ribbon STIR/SHAKEN solutions:
Service provider owned and deployed within the service provider’s network
Ribbon hosted STIR/SHAKEN
as a Service (S/SaaS)
Ribbon STIR/SHAKEN Solution - Deployed By Service Provider
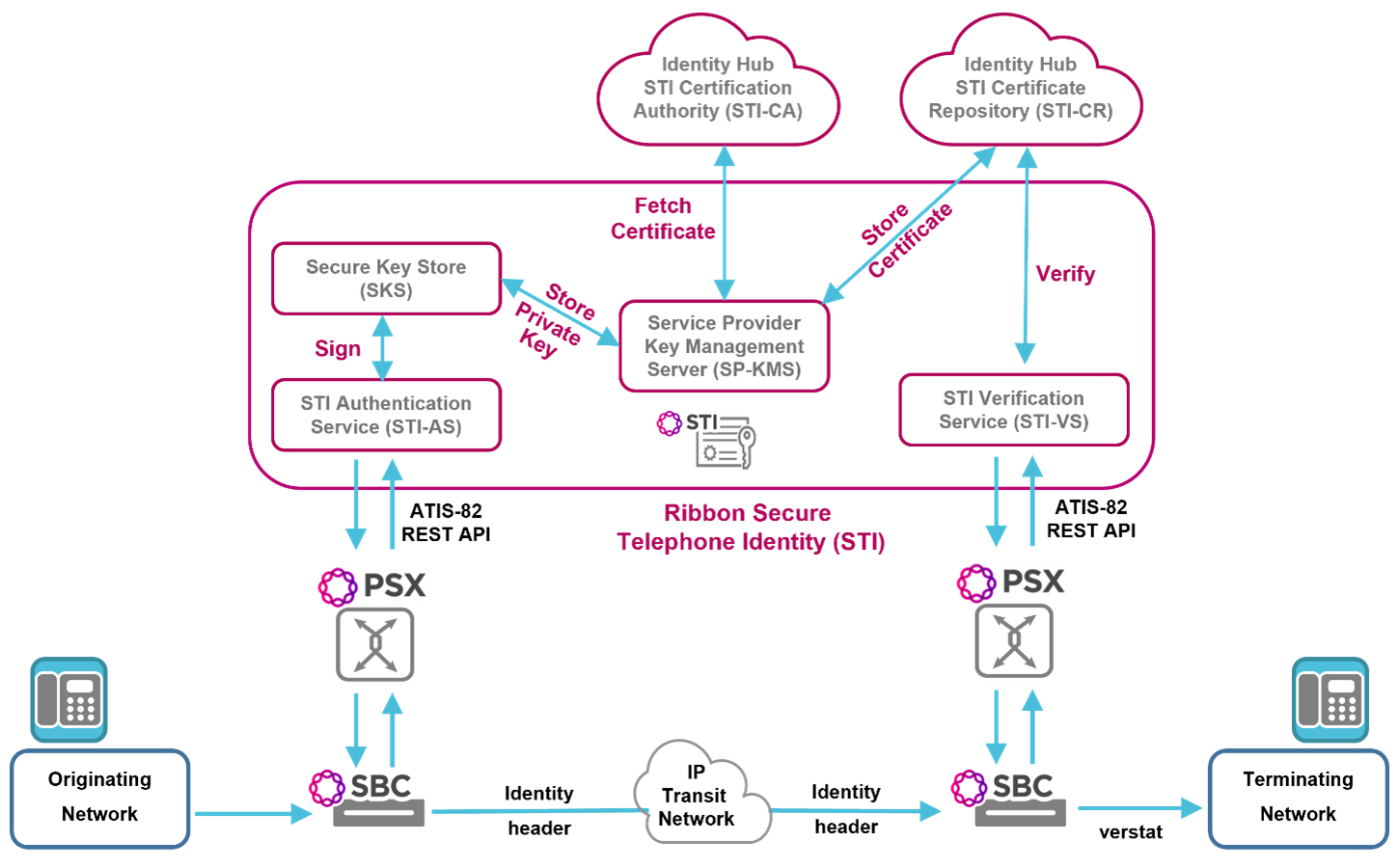
A part of Ribbon's Call Trust® portfolio, Ribbon offers voice service providers a complete STIR/SHAKEN solution. This solution encompasses all the components that are integral to, and required for, caller identity authentication, signing, verification and certificate management.
- Call controllers, session border controllers, and policy & routing servers that initiate call authentication or call verification requests and handle the responses from the Secure Telephone Identity (STI) domain
- Secure Telephone Identity - Authentication Service (STI-AS) and the associated functions of Service Provider Key Management Service (SP-KMS) and Secure Key Store (SKS) to process originating network requests for signed assertion of caller’s identity
- Secure Telephone Identity - Verification Service (STI-VS) and the associated function of Secure Telephone Identity Certificate Repository (STI-CR) to process terminating network requests for certificate verification of a caller’s identity. Note: Ribbon provides the STI-CR function as a cloud-hosted service on Ribbon Identity Hub
- Secure Telephone Identity – Certificate Authority (STI-CA) providing the following capabilities:
- Accept SHAKEN Certificate Signing Requests (CSRs) for new certificates
- Automatically validate Service Provider Code (SPC) Tokens and issue standards-compliant SHAKEN signing certificates that include the required Telephone Number Authorization List extension.
- Revoke certificates if needed and notify the Secure Telephone Identity – Policy Administrator (STI-PA).
- Note: Ribbon provides the STI-CA function as a cloud-hosted service on Ribbon Identity Hub
Ribbon STI is compliant with ATIS-1000082 and RFC8224/8225/8226. Ribbon STI implements the ATIS-82 server side specifications and can be deployed within a service provider’s network When deployed in an originating voice service provider’s network, Ribbon’s STI solution will receive call authentication requests, provide all the steps necessary to process these requests and respond with signed assertion of caller’s identity. Following STI authentication and signing, the signature information will be passed back to the authentication request originator to be forward to the next network hop.
When deployed in a terminating voice service provider’s network, Ribbon’s STI solution will receive call verification requests, provide all the steps necessary to process these requests and respond with the appropriate verification of caller’s identity. Following STI certificate verification, the verification information will be passed back to the verification request originator.
Request a STIR/SHAKEN Quote
Identity Assurance Explained
Identity Assurance Explained
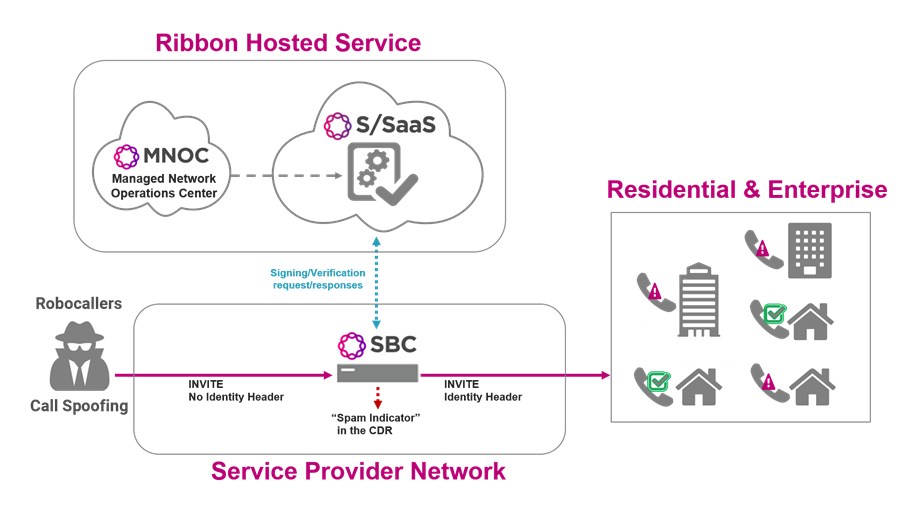
Ribbon STIR/SHAKEN as a Service
Select Ribbon’s STIR/SHAKEN (S/SaaS) solution to take advantage of a cloud-hosted managed service instead of implementing a STIR/SHAKEN-compliant Secure Telephone Identity solution within your own network. Allow Ribbon to take care of all the STIR/SHAKEN authentication, signing, verification, and certificate management services as described above. The service provider’s only obligation is to have a Session Border Controller (SBC) for interworking with the Ribbon hosted service. As part of the response to the SBC, Ribbon’s S/SaaS can instruct the SBC to perform a specific call validation treatment, based on the verification information.
This hosted service is offered by Ribbon in a standard SaaS model where the service is consumed on a usage basis.