Are You Sure Your Mobile Network is Secure?
NOTE: This is Part 2 of a 2 Part series covering the vulnerabilities in today’s mobile networks and how service providers can address them.
In the first part of this blog, I discussed the pervasiveness of mobile devices and some of the security vulnerabilities facing mobile service providers. In Part 2, I will describe in more detail the security challenges that many mobile network operators face and offer practical solutions regarding how they can address them.
The Challenge
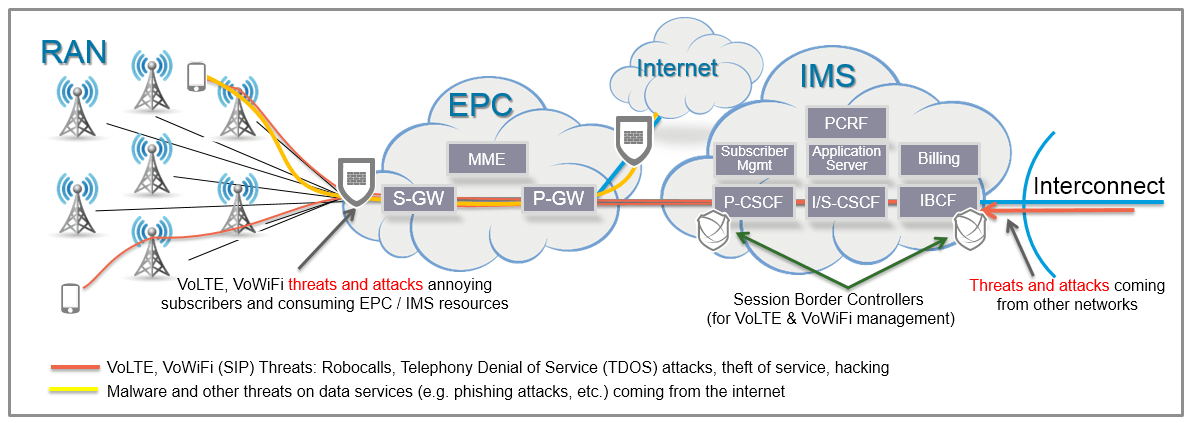
Today mobile network operators manage billions of VoIP minutes on their networks at peering points with other operators and deep within their IMS architectures for calls originating within their networks. Interconnection Border Control Functions (IBCF) are used at these edge network points to perform important call management and transcoding functions. Moreover, the IBCFs in a IMS architecture have the ability to protect the network from threats such as Denial of Service (DoS) attacks as well as decode and encode encrypted SIP signaling.
Proxy Call Session Control Functions (P-CSCF) serve as the entry point to the IMS domain and as the outbound proxy server for the endpoint device (e.g. smartphone). The P-CSCF protects against unauthorized IMS registrations and service abuse in which unauthorized users can use the services more than expected or gain access to services that are not allowed for them.
However, the challenge becomes how to further secure VoLTE traffic and mitigate bad actor infiltration and rogue endpoints generating DOS attacks, robo-calls, Telephony DoS (TDoS) attacks, network intrusions using SIP or having an endpoint device register to a fake application server.
With the growing demand of smartphones enabled for both VoLTE and VoWiFi, new openings have emerged for attacks – specifically with the data flows through the IMS Packet-Gateway (PGW) and the Serving Gateway (SGW). These elements were traditionally thought of as secure as they were facing the trusted Radio Access Network (RAN) and IMS core. Today next generation firewalls (NGFW) can be placed in the packet flow of these elements to protect against data attacks. However, traditional NGFW do not have deep visibility of SIP because they don’t understand SIP requirements such as the dynamic nature of opening and closing of ports based on SIP Signaling. In fact, in many cases SIP ALGs in NGFWs are turned off to allow VoWiFi and VoLTE calls to complete. This is a significant vulnerability in current mobile architectures that could result in subscriber exfiltration attacks, as well as attacks directly on the EPC and IMS infrastructure.
Figure 1: Today’s architecture: The IMS core for VoLTE, VoWiFi and VoIP call management
The Solution
To completely protect the VoLTE network starts with a deep understanding of attack vectors targeting VoLTE. With the wide varieties and inherent complexities of SIP and VoIP protocols, VoLTE networks can only stand to benefit from the added value of behavioral analytics and machine learning. Specific to the connected smartphone applications, behavior analysis combined with machine learning will be crucial for detecting many types of fraudulent activity. Whether it be in the core of the mobile provider network or delivered as a service to the end customer, behavioral analytics has an important role to play in securing these network environments.
How Would it Work?
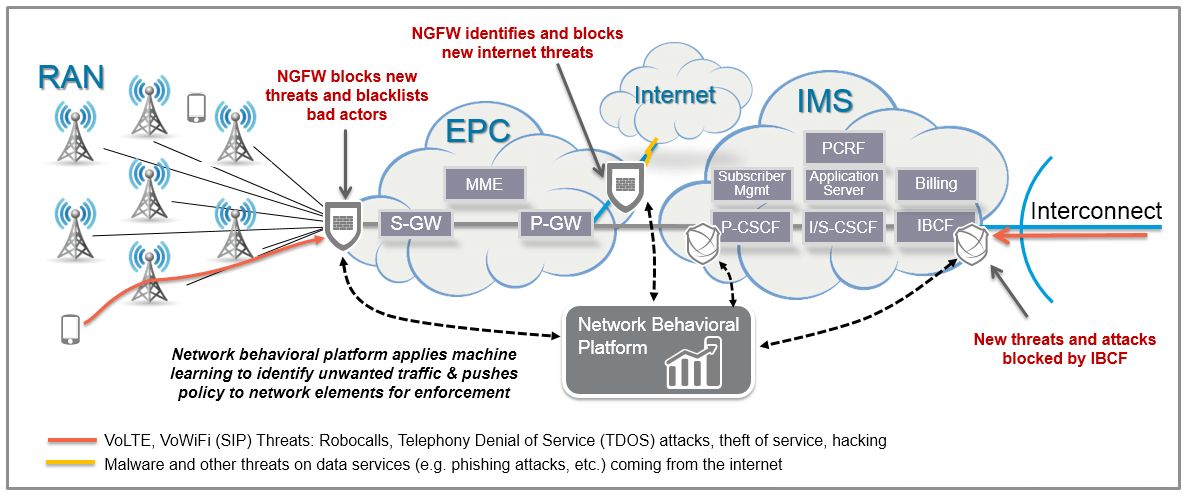
The IBCF’s position in the network is important as all VoLTE signaling traffic exchanged with peering partners must transit that platform. The IBCF inherently verifies the validity of the VoLTE and VoWiFi signaling protocols, provides user authentication, media protocol pin-holing (UDP and TCP) as well as understanding media protocol syntax and allowable bit-rates. As the IBCF is performing its core interconnection functions with peering partners, data about the VoLTE sessions, subscribers and routes are being logged and stored. A network behavioral analytics platform uses the IBCF as a “sensor” in the network. It gathers the collected data such as call detail records (CDRs), syslogs and event log data for analysis, trending and policy decisions.
Similarly, the P-CSCF’s position in the network is equally important as all VoLTE signaling and media traffic exchanged with access endpoints must transit the platform. End user smartphones must connect through the P-CSCF in which registration and service access metrics are logged and monitored. A network behavioral analytics platform would also use the P-CSCF also as a “sensor” in the network, capturing logged data for analysis, trending and policy decisions.
As this network behavioral analytics platform collects data from the network “sensors,” transactional and behavioral analytics are performed to develop a new unified policy-based set of security enforcement rules for VoLTE traffic. These new security policies are provided to the enforcement points, or “enforcers” in the network which are capable of actually securing or altering the nature of the traffic. For example, the P-CSCF becomes the “enforcer” detection point for DoS and BOT originated attacks from mobile endpoints. Applying network behavioral analytics to these traffic flows allows MNOs to be able to identify threats in ways that simply weren’t possible even one year ago.
Finally, the integration across disparate enforcement points – such as NGFW, SBCs, SDN enabled white box switches - enable this network behavioral analytics platform to signal these enforcement devices to block and blacklist unwanted traffic. Placing policy enforcement rules both at the ingress and egress points to the internet and between the Radio Access Network (RAN) and the Evolved Packet Core (EPC) means this unwanted traffic never consumes valuable capacity, thereby saving significant CAPEX and OPEX dollars for the MNO. In essence the network behavioral analytics platform becomes the security control plane for the network while the firewall, SBC or other elements become the enforcement points.
Figure 2: IBCF and P-CSCF provide input to network behavioral analytics platform on SIP flows which signals the firewall to take action against unwanted traffic
By using analytics on the data collected from existing IBCF and P-CSCF elements (“Sensors”) and applying recursive security policies back to those existing IBCF and P-CSCF elements (“Enforcers”), mobile network operators can reduce costs due to service abuse and provide a more secure subscriber experience against breaches such as toll fraud.
Differentiation is the Key to Success
As the mobile market shifts to 5G and billions more of new devices are being connected to mobile networks, security will become even more important to new IoT providers and consumers. Establishing and monetizing the mobile network as a security platform that can be leveraged by the next wave of applications will be an important game-changing differentiator for the mobile operator and their customers.